
by PCS | Jun 16, 2025 | 2025, Tips & Tricks
Not all audit findings are created equal. Major nonconformities can delay certification and signal serious issues in your ISMS. From unqualified auditors to poor risk assessment methods, these red flags must be addressed ASAP. #PinedaCyberSecurity...

by PCS | Jun 12, 2025 | 2025, Updates
This Independence Day, we honor the freedom our heroes fought for, and the responsibility we carry to protect it in every space (including the digital world)! Mabuhay ang malayang Pilipino! #PinedaCyberSecurity #CyberSecurityMakesSenseHere #PCSCyberEd...

by PCS | Jun 11, 2025 | 2025, Tips & Tricks
“You can’t manage what you don’t measure.” Security metrics are key to knowing if your cybersecurity efforts are working, and where to focus next. Whether it’s KPIs or compliance dashboards, the right data tells the story of your risk posture, performance,...

by PCS | Jun 10, 2025 | 2025, Tips & Tricks
Let’s break down the 3 main cloud service models and how they fit your needs—from plug-and-play apps to full control over infrastructure. Choose the right model, secure your data, and scale smarter! #PCSCyberEd #SecurityPlus #CloudSecurity #CyberAwareness #SaaS #IaaS...
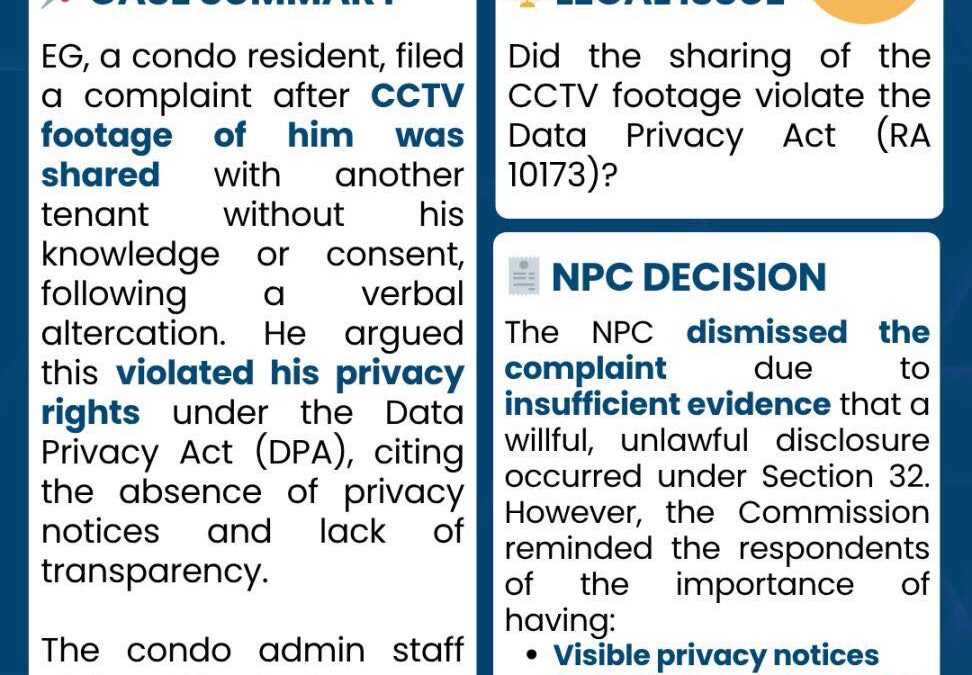
by PCS | Jun 7, 2025 | 2025, Tips & Tricks
Even if done in good faith, sharing CCTV footage without clear consent or notice can put an organization at risk of violating privacy laws. Residential communities must establish proper privacy protocols. #PinedaCyberSecurity #CyberSecurityMakesSenseHere #PCSCyberEd...









